Construction was among the top five business sectors targeted by cyberattacks in the second quarter of 2018, according to the latest “threat report” released earlier this month by eSentire, the largest pure-play managed detection and response service provider.
Based on intelligence gathered from more than 2,000 proprietary network and host-based detection sensors distributed globally in multiple industries, eSentire estimates that the number of attacks on Microsoft Internet Information Services (IIS) jumped to 1.7 million in the second quarter, from 2,000 in the first quarter. Most sources targeting IIS web servers originated from China-based IP addresses: according to Shodan, the global search engine for Internet-connected devices, there are 3.5 million IIS web servers exposed (with 1 million in China). The compromised servers largely originated from the Tencent and Alibaba sites.
eSentire observed IIS and WebLogic attacks originating from servers hosting Apache, RDP, SQL, IIS, and HTTP API services. Most of the records included known potential vulnerabilities based on server software version. Vulnerability records for attacking servers showed a steady increase. The majority of this growth appeared to come from Apache HTTP Servers, version 2.4.23. In the same period, records reporting vulnerabilities in IIS 7.5 and HTTP Server 2.4.10 appeared to diminish.
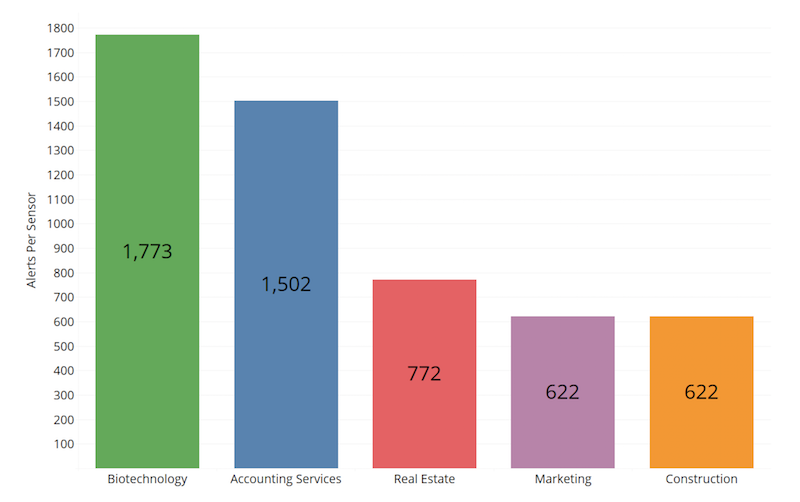
Four million potentially hostile events resulted in 57,000 alerts having been sent from eSentire’s SOC (Security Operations Center) between April 1 and June 30, 2018. Normalizing by sensor count, the top five affected industries were Biotechnology, Accounting Services, Real Estate, Marketing, and Construction. Regardless of industry, most attackers are probably looking to drive ad revenue or adopt compromised servers into their attack infrastructure, the report suggests.
The reason attacks continue, posits the report, is because most organizations have internal systems they hesitate to update for fear it will change or break something. These systems are sometimes accidentally exposed to background internet radiation which includes a firehose of exploits. Or, they are unaware that a patch is necessary or underestimate the gravity of failing to patch. This is an easily rectifiable problem that nevertheless lingers for many businesses.
There also was an increase, in general, in phishing attacks that used shipping invoice lures, despite an overall decline in the use of DocuSign—which facilities the exchanges of contracts and signed documents—as lures. Construction, Education, and Marketing experienced the largest amount of confirmed phishing attacks, with DocuSign dominating the lures observed; likely, these industries make frequent use of DocuSign in handling digital invoices and quotes due to remotely based business relationships and employees.
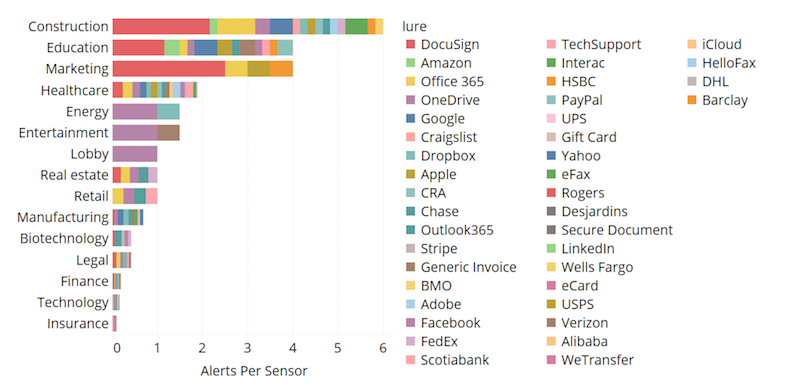
Construction was vulnerable to phishing attacks that used DocuSign as their primary lure. Image: eSentire
Real Estate experienced high volumes of D-Link home router exploit attempts. Marketing was subjected to a high volume of D-Link exploit attempts and a sizable degree of malicious PowerShell activity. And Construction experienced a large amount of Drupalgeddon2 attacks (the name given to an extremely critical vulnerability Drupal maintainers patched in late March).
PowerShell is a task-based command-line shell and scripting language built on .NET. PowerShell helps system administrators, and power-users can rapidly automate tasks that manage operating systems (Linux, macOS, and Windows) and processes. PowerShell commands let you manage computers from the command line.
In Q2 2018, the eSentire detection surface revealed that an obfuscated PowerShell realized an increase of 50% in commands, partly due to Emotet, a sophisticated malware.
Emotet, a four-year-old banking trojan, continues to evolve and emerge; antivirus solutions detected it, on average, only 22% of the time in the quarter. Emotet remains a popular choice for threat actors and was the most frequently observed malware due to numerous version updates and feature additions since it was first reported in 2014. Obfuscated malicious PowerShell commands increased 50% in Q2 2018.
Nearly half (49%) of Emotet samples included “invoice,” “payment,” or “account” in their file names. For Emotet’s competitor, Hancitor, fax documents were a popular lure (25%).
To protect against Emotet and to mitigate worming capabilities, Server Message Block Protocol (SMB) communications between systems in a network should be restricted via group policy settings or in the configuration of host-based Intrusion Prevention Systems (HIPS).
Malware, which is intended to damage or disable computers and systems, breaks down into four threat levels: malicious, suspicious, benign, and ambiguous (like false positives). Construction ranked fourth—behind Healthcare, Real Estate, and Marketing—for malware events (20 per sensor), and ranked second (after Accounting Services) for reputational blocks (about 5.25 alerts per sensor), which occur when known bad Internet Protocols (IPs) are detected trying to establish connections with monitored clients. Accounting Services and Construction are known to have large threat surfaces.
Some IPs only attempted an IIS or WebLogic exploit, while other IPs attempted both. The IPs attempting IIS and WebLogic persisted throughout the quarter, said eSentire, but those tended to rise with the emergence of other potential campaigns, indicating some threat actors may have an array of botnets in different configurations.
Related Stories
| Oct 13, 2010
Community center under way in NYC seeks LEED Platinum
A curving, 550-foot-long glass arcade dubbed the “Wall of Light” is the standout architectural and sustainable feature of the Battery Park City Community Center, a 60,000-sf complex located in a two-tower residential Lower Manhattan complex. Hanrahan Meyers Architects designed the glass arcade to act as a passive energy system, bringing natural light into all interior spaces.
| Oct 12, 2010
Guardian Building, Detroit, Mich.
27th Annual Reconstruction Awards—Special Recognition. The relocation and consolidation of hundreds of employees from seven departments of Wayne County, Mich., into the historic Guardian Building in downtown Detroit is a refreshing tale of smart government planning and clever financial management that will benefit taxpayers in the economically distressed region for years to come.
| Oct 12, 2010
Owen Hall, Michigan State University, East Lansing, Mich.
27th Annual Reconstruction Awards—Silver Award. Officials at Michigan State University’s East Lansing Campus were concerned that Owen Hall, a mid-20th-century residence facility, was no longer attracting much interest from its target audience, graduate and international students.
| Oct 12, 2010
Gartner Auditorium, Cleveland Museum of Art
27th Annual Reconstruction Awards—Silver Award. Gartner Auditorium was originally designed by Marcel Breuer and completed, in 1971, as part of his Education Wing at the Cleveland Museum of Art. Despite that lofty provenance, the Gartner was never a perfect music venue.
| Oct 12, 2010
Cell and Genome Sciences Building, Farmington, Conn.
27th Annual Reconstruction Awards—Silver Award. Administrators at the University of Connecticut Health Center in Farmington didn’t think much of the 1970s building they planned to turn into the school’s Cell and Genome Sciences Building. It’s not that the former toxicology research facility was in such terrible shape, but the 117,800-sf structure had almost no windows and its interior was dark and chopped up.
| Oct 12, 2010
Full Steam Ahead for Sustainable Power Plant
An innovative restoration turns a historic but inoperable coal-burning steam plant into a modern, energy-efficient marvel at Duke University.
| Oct 11, 2010
HGA wins 25-Year Award from AIA Minnesota
HGA Architects and Engineers won a 25-Year Award from AIA Minnesota for the Willow Lake Laboratory.
| Oct 11, 2010
MBMA Releases Fire Resistance Design Guide for metal building systems
The Metal Building Manufacturers Association (MBMA) announces the release of the 2010 Fire Resistance Design Guide for Metal Building Systems. The guide provides building owners, architects, engineers, specifiers, fire marshals, building code officials, contractors, product vendors, builders and metal building manufacturers information on how to effectively meet fire resistance requirements of a project with metal building systems.
| Oct 6, 2010
Windows Keep Green Goals in View
The DOE's National Renewable Energy Laboratory has almost 600 window openings, and yet it's targeting LEED Platinum, net-zero energy use, and 50% improvement over ASHRAE 90.1. How the window ‘problem’ is part of the solution.
| Sep 30, 2010
Luxury hotels lead industry in green accommodations
Results from the American Hotel & Lodging Association’s 2010 Lodging Survey showed that luxury and upper-upscale hotels are most likely to feature green amenities and earn green certifications. Results were tallied from 8,800 respondents, for a very respectable 18% response rate. Questions focused on 14 green-related categories, including allergy-free rooms, water-saving programs, energy management systems, recycling programs, green certification, and green renovation.